AWS CloudTrail is a service that enables recording of account activities against your AWS resources. It’s designed to enable auditing of your (AWS) account activities, and achieve requirements for governance and compliance by providing complete event history of actions taking place from AWS Management Console, SDKs, CLI, or directly from AWS resources.
Following picture shows a conceptual flow of how CloudTrail works:
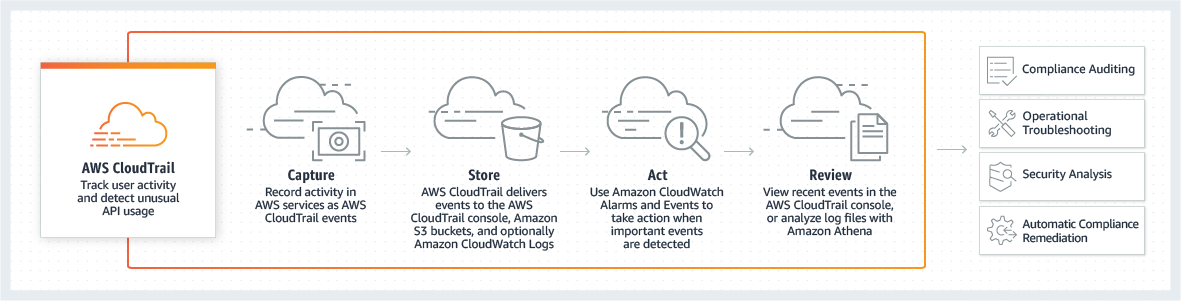
Image courtesy of AWS
AWS CloudTrail Events
A CloudTrail Event is a record of an activity in an AWS Account, as a result of an action taken by a User, Role, or Service (most AWS Services are supported, but not all).
Types of Events:
Management Events – captures management operations like creation, deletion, and modification of resources (such as EC2 instances).
- For such events, it records details like
- About who did it – AWS Account, IAM User / Role, and IP Address
- About what changed – time of the action, and what resources were affected
- Management Events record operations known as “control plane” operations
Data Events – captures operation-level details for resources (S3 and Lambda), such as:
- S3 – who (Accounts, User / Role, IP Address) accessed / changed the object; time and action details
- Lambda – who (User / Service) made the call; when (time), and what function was executed
- Data Events must be explicitly configured for specific (S3 / Lambda) resources or at resource type (S3, Lambda)
- Data Events can be very high volume activities
CloudTrail Insights Events – a special type of events that monitor write Management Events for abnormal activities
- Abnormal activities – when detected- are shown in the console, and delivered to S3 Bucket, CloudWatch Events, and optionally to CloudWatch Logs
- CloudTrail Insights uses machine-learning to analyze and detect abnormal behavior (such as more than usual activities, or unusual type of activities, missing periods of activities, etc.)
Record delivery is not real-time
- Typically CloudTrail delivers an event within 15 minutes of the API call
- CloudTrail delivers log files to S3 Bucket every 5 minutes – if there is any activity to report during that period
- Event data history is available in CloudTrail on a rolling 90 days basis
- CloudTrail log files (delivered to S3) are stored indefinitely be default, but you can configure it along with applying S3 object lifecycle rules
Key Points for AWS CloudTrail
- CloudTrail is enabled on all AWS Accounts and starts capturing activities (for create, modify, and delete) from the get-go, without you having to enable anything
- You can additionally configure to capture complete record of Account activities, including all management events, data events, and read-only activities.
- You can configure to get CloudTrail data from multiple Regions into a single S3 Bucket.
- In addition to default (of Logs delivered to S3), you can configure to deliver them to CloudWatch Logs and CloudWatch Events as well.
- CloudTrail supports log files’ integrity validation to check for any tampering (delete / modify), which is critical for auditing purposes
- Encryption – CloudTrail encrypts all log files delivered to S3 Bucket using S3 SSE, and you can additionally add a layer of encryption by using your KMS Key.
- S3 will automatically decrypt the log files if you have the right permissions
- CloudTrail provides filters – Event name, User name, Resource name, Event source, Event ID, and Resource type – to search against account activities
- CloudTrail can help in the areas of Compliance, Security related triage, track Users’ activities, operational issues triaging
- You can create up to 5 trails in a Region to allow each set of stakeholders (e.g., Auditors, Security Principals, etc.) to have their specifically configured trails for their needs
Pricing
AWS CloudTrail is billed for following components:
- Management Events – first copy of management events is provided free of charge.
- Additional copies – $ per 100,000 events
- Account activity for all management events in supported AWS services for the most recent 90 days is available for free of charge.
- Data Events – per 100,000 events
- CloudTrail Insights – per 100,000 events analyzed
External Resources